Sftp Port Specification

It is not a coincidence.
Sftp port specification. Ftp users may authenticate themselves with a clear text sign in protocol normally in the form of a username. We do this so that more people are able to harness the power of computing and digital technologies for work to solve problems that matter to them and to express themselves creatively. This is a story of how it got that port. Our software implements ssh version 2 sftp versions 3 4 and 6 scp and ftps according to publicly available standards.
It has been around since late 1990s. Sftp instructions july 5 2020 contents 1 introduction3 2 general sftp setup3. The file transfer protocol ftp is a standard network protocol used for the transfer of computer files between a client and server on a computer network. Our mission is to put the power of computing and digital making into the hands of people all over the world.
When i tatu ylonen first published this story in april 2017 it went viral and got about 120 000 readers in three days the story of getting ssh port 22. Ssh provides a secure channel over an unsecured network by using a client server architecture connecting an ssh client application. In computing the ssh file transfer protocol also secure file transfer protocol or sftp is a network protocol that provides file access file transfer and file management over any reliable data stream it was designed by the internet engineering task force ietf as an extension of the secure shell protocol ssh version 2 0 to provide secure file transfer capabilities. I wrote the initial version of ssh secure shell in spring 1995.
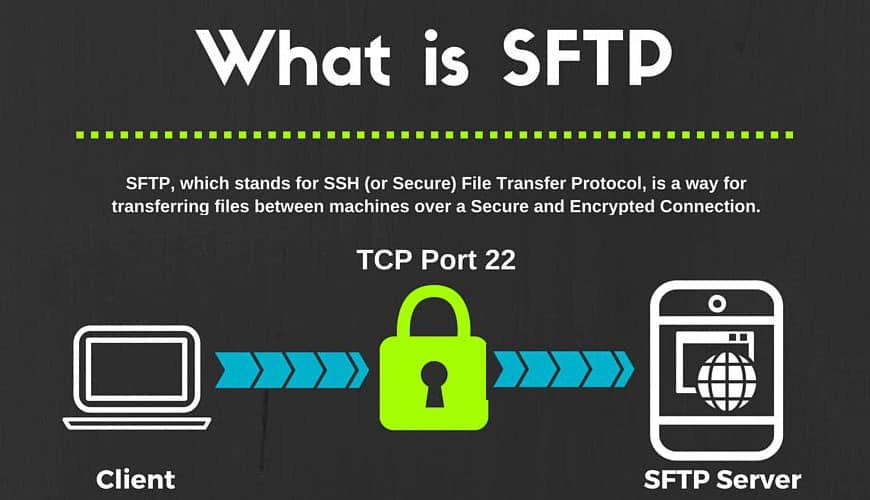
The default ssh port is 22. On unix like operating systems a process must execute with superuser privileges to be able to bind a network socket to an ip address using one of the well known ports. Sftp almost always runs over an ssh session usually on tcp port 22. How ssh port became 22.
The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well known ports or system ports. Typical applications include remote command line login and remote command execution but any network service can be secured with ssh. They are used by system processes that provide widely used types of network services. Ftp is built on a client server model architecture using separate control and data connections between the client and the server.
In addition our software supports minor extensions documented here. Secure shell ssh is a cryptographic network protocol for operating network services securely over an unsecured network.